Team-BHP
(
https://www.team-bhp.com/forum/)
At this point in lifetime of Internet, the very definition of Internet is under 'consideration' (read attack). Because we don't have well defined laws dealing specifically with Terms and Quality of service provided by ISPs and pretty much anything in general, it is left to interpretation of every individual and entity.
I am not an expert on copyright and IP laws but as far as I can understand, any content loaded by a particular URL has to be the IP of the owner of that URL so any 'modification' should amount to IP violation.
There are ways to by pass this. As suggested by Rehaan, 'https' takes care of this injection. By encrypting the stream of data you take away the ability of ISP to be the 'man-in-the-middle' (which is illegal) because if they can't read the structure of HTML loaded by that URL, they can't inject their scripts. Although, security of 'https' as a standard/protocol itself is under attack. Also, this puts the onus on the website owners as ultimately they have to support https and https has significant computational power (means money) overhead
There are other ways as well. Using AdBlocking extensions in your browser is one way. Here is one for Chrome:
https://chrome.google.com/webstore/d...ibdccddilifddb and you can use this for firefox:
https://addons.mozilla.org/en-us/fir.../adblock-plus/
(And no, don't use internet explorer, it's security is as leaky as a hose on a 70s range rover)
At browser level itself you should always keep the browser updated to the latest version. Mozilla and Google keep on fixing holes and breaches. To give you an example, the 'iframe-ing' example provided by rehaan has actually been fixed, at least in higher upstream versions of Firefox and Chrome (I know, I just said whole lot that is written in English but doesn't read in English at all)
If you're the good kind of paranoid who can spend money, there are internet routers available that can take care of a lot. As suggested by mayankk you can add URLs to block at router level; there are routers that can download filter lists from internet and use them to block shady/malicious URLs.
Lastly, we need to continue to be litigant about this whole mess. Internet neutrality, content injection, usage pattern analytics all tie in together somewhere and we need to maintain status quo of internet as we know and love. Big Businesses have always tried to be sly and tricky while providing services but as those Govt Ads say: "Jaago Grahak, Jaago"
I'm no techie, so I was wondering how different this is from what Google does?
AFAIK,they do ask for our permission before they collect anonymous data unlike these ISPs. So other than that ?
Quote:
Originally Posted by shashank.nk
(Post 3749754)
I'm no techie, so I was wondering how different this is from what Google does?
AFAIK,they do ask for our permission before they collect anonymous data unlike these ISPs. So other than that ?
|
Difference is that, they display Ads as part of content of their own websites. To make it more clear and make you more angry, what airtel is doing would be something like Google using chrome to embed their ads in some random websites. For example, you open bing.com in chrome but because you use google's chrome so they replace bing.com content with google content.
Do these ads work on a HTTPS connection as well ? What about when you use Google DNS or Open DNS ?
Quote:
Originally Posted by shashank.nk
(Post 3749754)
I'm no techie, so I was wondering how different this is from what Google does?
AFAIK,they do ask for our permission before they collect anonymous data unlike these ISPs. So other than that ?
|
Google collects a lot of data about you and me. They do that through their websites, through third party websites based on your surfing behavior and even from the android phones that basically mine through your emails, SMS etc. This huge volume of data then helps create your profile that helps them "address you" better. There is though an important thing to note here. Google is a reputed organization that has a very well defined and published privacy policy. It has clearly defined and declared the kind of data they collect and the what they do not collect. They also define how they share that data and with whom.
However, your ISP routing your traffic to some shady ad company in Timbaktu that reads all the contents being returned to you and embedding advertisement in the content is not exactly the same. You will not like it one bit when you realize that a man in mask is peering over your shoulders when you are logged in to your bank account or transferring funds or reading private or personal emails etc. This man in mask has no declared privacy policy. Heck for that matter, he does not even lets you know that he is lurking in the shadows. You do not know what kind of havoc he can break lose with all the financial and other private data that he is collecting when your surf.
In other words, it is the difference between a policeman with a gun vis a vis a man in a dark alley with a gun. You do not know who he is or what his motives are... Even a policeman can go astray. However, generally you will not panic when you see a policeman has a gun which you will with our proverbial man with a mask.
Quote:
Originally Posted by MHG
(Post 3749770)
Do these ads work on a HTTPS connection as well ? What about when you use Google DNS or Open DNS ?
|
No they shouldn't work with a full HTTPs request but it might if there are some insecure elements in the HTML of the page. Any URL in the browser may send 10s or 100s of subsequent requests to load the entire page and some of them(especially scripts), if sent over HTTP instead of HTTPs can also allow injection as well. Take a look at this screenshot of chrome:
http://i.stack.imgur.com/WC6a7.png. That yellow triangle means partially secure request.
Using reliable public DNS services is always a good practice as ISPs are known to hijack DNS requests.
Do these additional bytes count towards our usage? I use Airtel, and they have a limit (Fair Usage Policy) beyond which their mediocre speeds become even slower.
Security is a major concern what with most of us transacting online. I'm also worried they're taking us for a ride by artificially bumping up our usage/consumption.
I'd say this is OK even though it's isn't acceptable,until you use a MTS connection where 6 out of 10 times on going to a different webpage or browsing through a forum including Team-Bhp and also when you are in the middle of an Online Transaction,you will invariably end up in their homepage and it returns back to the same MTS homepage even if you try to reload.
It can get annoying at times as it is very frequent.
Oh my God, you find this surprising? Trust me there are a million things which a lot of people don't know about when it comes to data collection. Have U ever thought that an innocuous looking (from a famous brand) app sitting on your mobile might be actually collecting data, or it might be listening to certain signals coming from some other devises in your house and targeting ads on those basis. There are ways to even record conversations and then upload them to servers for analysis without the user even coming to know of it?
The online advertising world is super advance in targeting users. Brands (big, medium & small) are ready to pay big bucks to any company that can reach out to their target audiences accurately.
Ever wondered why that Domino's or Amazon ad starts following you as soon as you visit the site, say even for a few seconds? Next time look carefully at the Amazon banner and you will be amazed at what it shows you. If you have figured it out do share it here for the benefit of all.
Lastly...If you are travelling for a day, try and check the brand ads from major pizza chains in both cities, trust me you will be amazed!
Quote:
Originally Posted by needmorebhp
(Post 3749784)
No they shouldn't work with a full HTTPs request but it might if there are some insecure elements in the HTML of the page. Any URL in the browser may send 10s or 100s of subsequent requests to load the entire page and some of them(especially scripts), if sent over HTTP instead of HTTPs can also allow injection as well. Take a look at this screenshot of chrome: http://i.stack.imgur.com/WC6a7.png. That yellow triangle means partially secure request.
Using reliable public DNS services is always a good practice as ISPs are known to hijack DNS requests.
|
Interesting. Plenty are the ways these nefarious ISPs can adopt to harass innocent users.
Team-BHP has some trouble with HTTPS though. All navigation links, including the "you have been quoted" message I got because you replied to my post are HTTP. I login via HTTPS but on following a HTTP link it shows me as a user who has logged out. I need to manually prefix https:// in the address bar to reply to a post.
Switching assets over to HTTPS is harder to solve I guess. Easiest if the site commits to using 100% HTTPS.
The ads from google etc were already irritating enough. But to have the ISPs monitor our activities is almost like someone watching us bath.
Quote:
Originally Posted by needmorebhp
(Post 3749784)
No they shouldn't work with a full HTTPs request but it might if there are some insecure elements in the HTML of the page.
Using reliable public DNS services is always a good practice as ISPs are known to hijack DNS requests.
|
Yep, I've read elsewhere that using a reliable DNS service solves this. On another note I'm using Idea wi-fi broadband here in Pune. I've been using the adblock plus and openDNS and many a times I've been warned of genuine-looking malicious sites.
When using a secure connection to the T-BHP site (
https://www.team-bhp.com), Chrome still says that while the connection is secure, there are other resources that are not secure.
Does this imply that while content coming in from the TBHP server go through a Secure connection, other plug-in content (like ads) are still being rendered via an unsecure (open, and therefore Vulnerable) connection ?
Quote:
Originally Posted by Lalvaz
(Post 3749391)
All the more shameful and surprising that this is coming from MTNL, if the government operators behave in an illegal manner, then what can one expect from the private players?
|
My guess is that most of the people responsible at MTNL don't truly understand what's happening here, and how much of a violation it is.
Most users don't either - that's the part I'm trying to address here.
Quote:
Originally Posted by mayankk
(Post 3749420)
I thought since its been blocked at the router level, all to and from is stopped?
|
If you do this, the ads won't display - but your data has still been shared with a shady 3rd party who could be using it for anything else.
Quote:
Originally Posted by dar3dev|l
(Post 3749574)
Just curious to know, is Team-bhp completely on Https ?
|
The site is accessible on httpS, however, there are still some unsecured elements. We need to work on that.
Quote:
Originally Posted by varunanb
(Post 3749687)
Many organizations have invested in e-commerce as the future of all bussiness and now with most cash transactions are online, a layman like me has no chance to identify right and wrong.
|
Most of these sites enforce secure connections (you'll see the green lock in your address bar), however, there's still a lot of not-perfectly-implemented setups out there - especially since ecommerce is now so widespread.
Quote:
Originally Posted by needmorebhp
(Post 3749731)
At this point in lifetime of Internet, the very definition of Internet is under 'consideration' (read attack).
|
Exactly! This is what's bothering me most.
There's a saying something like:
If you drop a frog in boiling water, it will jump out.
But if you put a frog in water, and then heat it slowly, it boils to death.
That's a good analogy for a lot of things that are happening to the Internet these days! (And needless to say, we're the frogs).
Quote:
Originally Posted by shashank.nk
(Post 3749754)
I'm no techie, so I was wondering how different this is from what Google does? AFAIK,they do ask for our permission before they collect anonymous data unlike these ISPs. So other than that ?
|
In a nutshell:
- Google informs the users (every site's privacy policy + t&c has info added to it if they use adsense).
- Google is much more likely to be following laws than an Adphonso -- who attained the data in this shady way in the first place.
- Google offers you an "opt out" of most of their programs.
- Google's ad network goes to benefit the website owners & content creators -- not the service provider who is already being paid by the customer.
Quote:
Originally Posted by MHG
(Post 3749770)
Do these ads work on a HTTPS connection as well ?
|
Probably not on a secure connection. Though they have been seen on a secure connection that used some unsecure elements.
Quote:
Originally Posted by MHG
(Post 3749770)
What about when you use Google DNS or Open DNS ?
|
Won't make a difference -- as that data is still coming through MTNLs servers, regardless of how your computer finds the IP address of the website.
This is pretty disheartening stuff, however, the people attacking Google are misdirecting their anger. Google has a very good privacy policy, and has monetised several properties very well. You, as an Android/Gmail/Google Docs/Calendar/Youtube/Search user are giving your data to Google so that YOU get more relevant advertisements and are served relevant content.
Yes, this seems a little shady, but if you embrace it, you will find useful links all around. You can also change all these settings from your Google account and send a DO NOT TRACK request for the same. However, if you let Google help you, it really can be very nice. I get on my Android phone, the location of where I have parked, the travel time for my common destinations (home, office, friends, clients), articles I might find interesting (based on my search history) which leads me to news about cars, Jeremy Clarkson, T-BHP news/articles that are trending, and so on. I can disable this for the sake of my privacy, but since Google already knows everything about me, I might as well let them help me! :D
Alternatively, you could simply install an AdBlocker, your data will still be collected, but you won't see any of the advertisements. Having said that, using an Ad Blocker harms the website you are visiting. If I block the advertisements on T-BHP, I am not being fair to the website by consuming free data, and blocking a source of revenue for the website, which is usually essential for publishers to survive. Anyway, as someone who works in digital marketing/advertising, my views on ad blocking tools are very poor, to say the least. :p
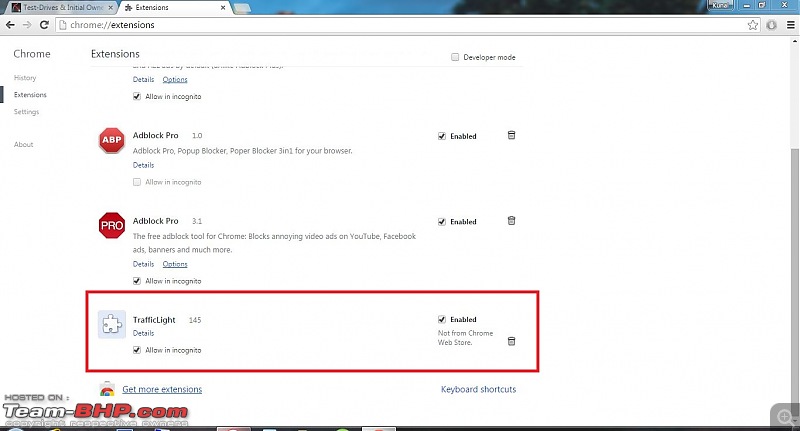
Similar spam advertisements also started coming around a month back or so on my laptop.
I use Google Chrome on Windows 7 and my ISP is BSNL Broadband.
The first time these ads came, I noticed that in my Chrome, certain unknown extension automatically gets installed and an unknown program is also showed in Add or Remove Programs list on Control Panel. Screenshots attached.
I installed Adblock extension just to remove these ads but even that didn't help.
Uninstalling the unknown extension as well as program solves the problem for me but after few days later similar extension and programs comes back again but with a different name. The most recent being today. :deadhorse
I am not a very technical person but would advice all those who are facing similar issues kindly check for any unknown web extensions in your browser and any unknown program.
Though the adds which I got were more or less similar to what Rehan has posted in the opening post but today I got something like this.


| All times are GMT +5.5. The time now is 13:40. | |




